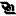-
-
Notifications
You must be signed in to change notification settings - Fork 134
HelpAddonsFuzzConcepts
Fuzzing is a technique of submitting lots of invalid or unexpected data to a target.
ZAP allows you to fuzz any request still using:
- A build in set of payloads
- Payloads defined by optional add-ons
- Custom scripts
To access the Fuzzer dialog you can either:
- Right click a request in one of the ZAP tabs (such as the History or Sites) and select “Attack / Fuzz…”
- Highlight a string in the Request tab, right click it and select “Fuzz…”
- Select the “Tools / Fuzz…” menu item and then select the request you want to fuzz
Payload Generators generate the raw attacks that the fuzzer submits to the target application.
They are managed via the Payloads dialog
Payload Processors can be used to change specific payloads before they are submitted.
They are managed via the Payload Processors dialog
Fuzz Location Processors can be used to change all of the payloads before they are submitted.
They are managed via the Location Processors dialog
Message Processors can access and change the messages being fuzzed, control the fuzzing process and interact with the ZAP UI.
They are managed via the Fuzzer dialog 'Message Processors' tab.
This functionality is based on code from the OWASP JBroFuzz project and includes files from the fuzzdb project. Note that some fuzzdb files have been left out as they cause common anti virus scanners to flag them as containing viruses. You can replace them (and upgrade fuzzdb) by downloading the latest version of fuzzdb and expanding it in the 'fuzzers' library.
| Fuzzer options screen |
-
 ZAP User Guide
ZAP User Guide
- Introduction
-
Getting Started
- Configuring proxies
-
Features
- Active Scan
- Add-ons
- Alerts
- Anti CSRF Tokens
- API
- Authentication
- Break Points
- Callbacks
- Contexts
- Data Driven Content
- Filters
- Globally Excluded URLs
- HTTP Sessions
- Man-in-the-middle Proxy
- Modes
- Notes
- Passive Scan
- Scan Policies
- Scope
- Session Management
- Spider
- Statistics
- Structural Modifiers
- Structural Parameters
- Tags
- Users
- Scanner Rules
- A Simple Penetration Test
-
The User Interface
- Overview
- The Top Level Menu
- The Top Level Toolbar
- The Tabs
-
The Dialogs
- Active Scan
- Add Alert
- Add Break Point
- Add Note
- Encode/Decode/Hash
- Filter
- Find
- History Filter
- Manual Request Editor
- Manage Add-ons
- Manage Tags
-
Options
- Active Scan
- Active Scan Input Vectors
- Alerts
- Anti CSRF Tokens
- API
- Breakpoints
- Callback Address
- Certificate
- Check for Updates
- Connection
- Database
- Display
- Dynamic SSL Certificates
- Extensions
- Global Exclude URL
- HTTP Sessions
- JVM
- Keyboard
- Language
- Local Proxies
- Passive Scan Rules
- Passive Scan Tags
- Passive Scanner
- Rule Configuration
- Scripts
- Search
- Spider
- Statistics
- Persist Session
- Resend
- Scan Policy Manager
- Scan Progress
- Session
- Spider
- The Footer
- Command Line
- Add Ons
- Releases
- Paros Proxy
- Credits