If you ha e questions and/or you need more infos on the project, pelaste contact [email protected].
From 01/01/2015 the project is part of broader YORI srl Project ! <img src="http://www.yoroi.company/images/logo.svg" alt="Yoroi" width="50" height="50" aligh="center" vertical-align:"bottom"/>
Gathering open data from malware analysis websites is the main target of Malware Control Monitor project. Visualize such a data by synthesize statistics highlighting where threats happen and what their impact is, could be useful to identify malware propagations
We actually scrape the following services:
If you are a malware scan provider and you would like to actively partecipate to the project by giving some of your data, please contact us, we'll be glad to add your service to our project. Each visualized threat comes with the original and 'clickable' URL pointing to the original report. The original report owns all the specific information to the threat.
It would be great having the opportunity to publish a live version of MalControl Center.
To accomplish this task we need one of the following:
- Money Donation (GitTip, preferred channel [see badget Mania for our current income in GitTip]]) in order to buy domain and hosting
- Hosting Donation.
It would be great having the opportunity to spend more time in developing this project in order to build an amazing Open Source platform able to grab most of the freely available infos on Malware and Threats showing them to the entire world with no fee or charges. To accomplish this task we need one of the following:
- Little money donations (GitTip, preferred channel)
- Helping us in developing MalControl. Please contact me !
In order to run MalControl on your own, you need to install:
- NodeJS: nodejs web site
- Mongo DB: installing mongodb
- git: installing GIT
Once you've installed the required software, it's time to clone that repository and to install dependencies:
git clone [email protected]:marcoramilli/malcontrol.gitcd malcontrol.gitnpm install
You need to configure the conf/configs.json file at your will. For example you need to add your own mapbox key. MapBox Key are free (under specific conditions) please take a look to https://www.mapbox.com
Now it's time to launch it !
gruntnpm start- go to localhost:8080
A backround node scrapes websites to grab malware informations and fills up a mongod database. An API node serves API useful to frontend layer. Public API are available, please read doc/index.html for a full list of API. If you are interested on developing a website scraper take as example one of the scrapers available into the scrapers folder. Each scraper must be a function 'goScraper' ending-up saving scraped data to db using the functionsaveMalwareToDB respecting the db schema placed into schemas/
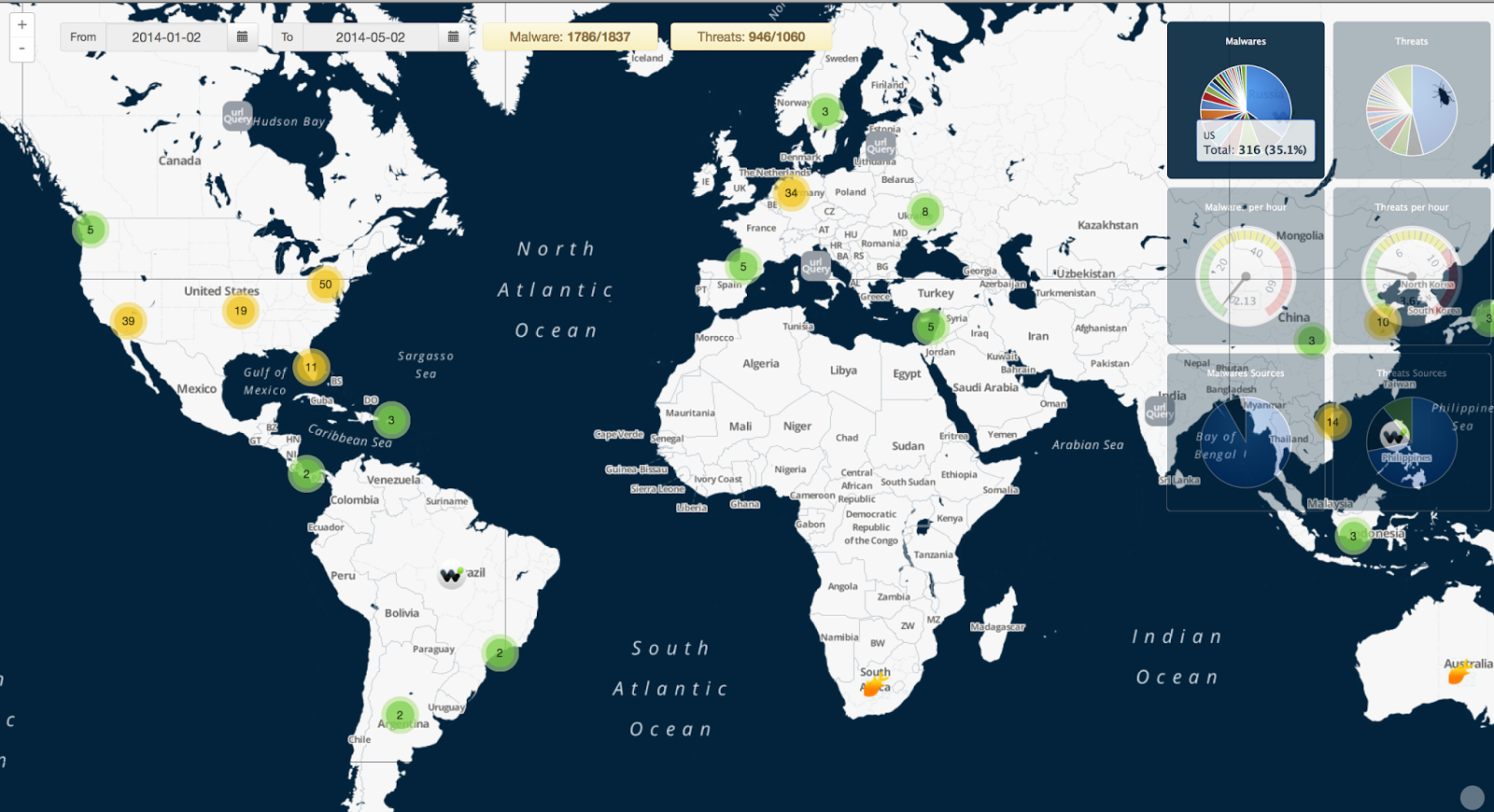
A world map displays, through the use of markers, the locations of all geolocalized malwares and threats detected by the scrapers. Every single marker has the shape of the logo of the scraped source of origin. Markers can be grouped, zoom map to see detailed information. Some useful charts are displayed on the right side showing all the information supplyed by backend's API.
Screenshots talk laudly :) The following image shows how MalControl geolocalize malware and threts by grouping them by country. On the rigth side of the screen graphs with transparent gradient shows trends and totals of the analized sources. The top two charts show the "top countries" spreading malware/threats.
The second top two charts shows how many malware/threats per hour Malcontrol is able to capture. This feature gives an instant view on how the "malware world" is progressing. The last two charts show the totals of malware/threats coming from the scraped sources. If you are interested on adding a source (by writing a scraper) please make a pull request or contact us.
By drilling down into a specific malware/threat you will see the icons of the scraped sources. By clicking on such icons a tooltip pops-up within detailed informations on the selected malware/threat. The imformations are source specific and might be different from source to source. The following image shows you detailed information on a PhishTank which provides Malicius URL and Report specific Report.
The following video shows how malcontrol is supposed to work. Please note the frontend might change overtime and the video might be outdated
Please refer to doc section for a fully documented Public API